# Network scanner
- there Discover all devices on the network
- Display there IP addresss
- Display there MAC address
#CODES
- ifconfig
 |
| the virtual interface created by virtual box/when we use kali machine to use nat network! #VM THINK THAT IT IS CONNECTED TO A WIRED NETWORK |
- netdiscover -r 10.0.2.1/16
#ARP protocol
ARP-ADDRESS RESOLUTION PROTOCOL
A very simple protocol that allows us to link IP addresses to MAC addresses.
0R translate IP addresses to MAC addresses.
# HOW ARP WORKS!- It sends a broadcast message/ARP request in a whole network it is known as broadcast MAC address
- When a packet is set to be sent to the broadcast MAC address all clients on the same network will receive this packet
- Now all of these devices will ignore this packet except the one that has this IP address which is 10.0.26/Device-C
- This way device A will have the MAC address of device C and now it will be able to communicate with device C and do whatever task that it wanted to do initially.
USING SCAPY WITH ARP TO DISCOVER ALL CLIENTS IN THE NETWORK
#CODE
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- scapy.arping(ip)
- scan("10.0.2.1/16")
- By using scapy.arping(ip)
- we easily discover the clients
- but this is SHORT-CUT!!
# SO WE ARE MAKING OUR OWN ALGORITHEMNSTEAD OF USING scapy.arping(ip)
# NETWORK SCANNER ALGORITHM
# GOAL - TO DISCOVER CLIENTS ON THE NETWORK
#1.Creat ARP request directed to broadcast MAC asking for IP
#2. Send a packet and receives a response
#3.Parse the response
#4.Print result
#1.Creat ARP request directed to broadcast MAC asking for IP
#1.1 _Use ARP to ask who has target IP
#1.2 _Set destination MAC to broadcast MAC
1.1 _Use ARP to ask who has target IP
#CODE
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP()
- print(arp_request.summary())
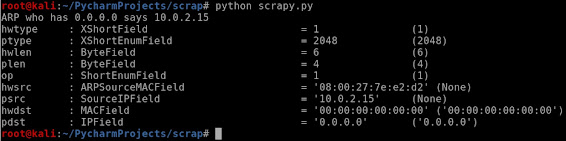
- scapy.ls(scapy.ARP()) #used to seclect the field
- scan("10.0.2.1/16")
- pdst: IPField = '0.0.0.0' ('0.0.0.0') / CUZ
- ARP who has 0.0.0.0 says 10.0.2.15 /in terminator
#CODE
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- print(arp_request.summary())
- scan("10.0.2.1/16")
| Our ARP is saying who has this IP("10.0.2.1/16") which is the IP that we're passing and it and saying to return the result to("10.0.2.15") |
NOW creating an Internet frame that will be sent to the broadcast. MAC address
#CODE:
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether()
- scapy.ls(scapy.Ether()) #used to seclect the field
- scan("10.0.2.1/16")
#CODE:
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- print(broadcast.summary())
- scan("10.0.2.1/16")
#CODE:combining the both code!
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- arp_request_broadcast = broadcast/arp_request
- print(arp_request_broadcast.summary())
- scan("10.0.2.1/16")
#TERMINALroot@kali:~/PycharmProjects/scrap# python scrapy.py
Ether / ARP who has Net('10.0.2.1/16') says 10.0.2.15#---.show() # use to just show in MORE details!
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- arp_request.show() # use to just show in details!
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- broadcast.show()
- arp_request_broadcast = broadcast/arp_request
- arp_request_broadcast.show()
- scan("10.0.2.1/16")
#TERMINALroot@kali:~/PycharmProjects/scrap# python scrapy.py
###[ ARP ]###
hwtype = 0x1
ptype = IPv4
hwlen = 6
plen = 4
op = who-has
hwsrc = 08:00:27:7e:e2:d2
psrc = 10.0.2.15
hwdst = 00:00:00:00:00:00
pdst = Net('10.0.2.1/16')
###[ Ethernet ]###
dst = ff:ff:ff:ff:ff:ff
src = 08:00:27:7e:e2:d2
type = 0x9000
###[ Ethernet ]###
dst = ff:ff:ff:ff:ff:ff
src = 08:00:27:7e:e2:d2
type = ARP
###[ ARP ]###
hwtype = 0x1
ptype = IPv4
hwlen = 6
plen = 4
op = who-has
hwsrc = 08:00:27:7e:e2:d2
psrc = 10.0.2.15
hwdst = 00:00:00:00:00:00
pdst = Net('10.0.2.1/16')#2.Send a packet and receives a response#CODE:#HOW TO USE sr/srp FUNCTION IN SCAPY
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- arp_request_broadcast = broadcast/arp_request
- answered, unanswered = scapy.srp(arp_request_broadcast, timeout=1)
- print(answered.summary())
- scan("10.0.2.1/16")
READ IN MORE DETAILS
- SO WE USE answered, unanswered AS VAIRIABLES
- TIMEOUT is very important or the cammand will never exit
#CODE:print(answered.summary())
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- arp_request_broadcast = broadcast/arp_request
- answered, unanswered = scapy.srp(arp_request_broadcast, timeout=1)
- print(answered.summary())
- scan("10.0.2.1/16")
#CODE:print(unanswered.summary())
WE GET MAC ADDRESS LIKE 52:54:00:12:35:00 /IP=10.0.2.1 #CLICK TO VIEW THE RESULTUNANSWERD SAYS THAT: THIS IPS ARE NOT USED BY ANY CLINETS ON NETWORK/THERE ARE CLINETS USING THEM#3 Parse the response#CODE:
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- arp_request_broadcast = broadcast/arp_request
- answered_list = scapy.srp(arp_request_broadcast, timeout=1)[0]
- for element in answered_list:
- print(element[1].show())
- print("--------------------------------------------")
- scan("10.0.2.1/24")
- line-8/- [0] = used cuz we need just answered / answerd, unanswered /-[0], [1]
- line-9/- for element in answered_list:= for/in is used to get the elements/its a LOOP
- line-10/- print(element[1].show()) /EXPLANATION!
# See the 1st packet in the terminal
(<Ether dst=ff:ff:ff:ff:ff:ff type=ARP |<ARP pdst=10.0.2.1 |>>,
<Ether dst=08:00:27:7e:e2:d2 src=52:54:00:12:35:00 type=ARP |
<ARP hwtype=0x1 ptype=IPv4 hwlen=6 plen=4 op=is-at hwsrc=52:54:00:12:35:00
psrc=10.0.2.1 hwdst=08:00:27:7e:e2:d2 pdst=10.0.2.15 |<Padding
load='\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00' |>>>)# THE COMA SEPERATES [0] / [1][0] = (<Ether dst=ff:ff:ff:ff:ff:ff type=ARP |<ARP pdst=10.0.2.1 |>>[1] = <Ether dst=08:00:27:7e:e2:d2 src=52:54:00:12:35:00 type=ARP |<ARP hwtype=0x1 ptype=IPv4 hwlen=6 plen=4 op=is-at hwsrc=52:54:00:12:35:00
psrc=10.0.2.1 hwdst=08:00:27:7e:e2:d2 pdst=10.0.2.15 |<Padding
load='\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00' |>>>)# SO WE NEED [1] HENCE USED /- print(element[1].show())
print(element.show())
print(element[1].show())#CODE:
- #!/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- arp_request_broadcast = broadcast/arp_request
- answered_list = scapy.srp(arp_request_broadcast, timeout=1)[0]
- for element in answered_list:
- print(element[1].psrc)
- print(element[1].hwsrc)
- print("--------------------------------------------")
- scan("10.0.2.1/24")
- hwsrc = HARDWARE SORCE/ MAC addres of the clinet that send the packet back to us
- psrc = sorce IP that the packet was sent from
#CODE:TERMINAL!root@kali:~/PycharmProjects/scrap# python scrapy.pyBegin emission:Received 529 packets, got 3 answers, remaining 253 packets10.0.2.1 #IP52:54:00:12:35:00 #MAC ADDRESS--------------------------------------------10.0.2.252:54:00:12:35:00--------------------------------------------10.0.2.308:00:27:2e:d3:9f
#4.Print result#CODE:
# !/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- arp_request_broadcast = broadcast/arp_request
- answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0]
- print("IP\t\t\tMAC Address\n--------------------------------")
- for element in answered_list:
- print(element[1].psrc + "\t\t" + element[1].hwsrc)
- scan("10.0.2.1/24")
Received 529 packets, got 3 answers, remaining 253 packets"
- verbose=False = USED TO HIDE = Begin emission:
- \t = USED FOR PUT SPACE/TAB BETWEEN TWO THINGS
- \n = GO GO DOWN IN LINE
- REMEMBER THAT 8/9/10 IS A PART OF THE LOOP
root@kali:~/PycharmProjects/scrap# python scrapy.py
IP MAC Address
--------------------------------
10.0.2.1 52:54:00:12:35:00
10.0.2.2 52:54:00:12:35:00
10.0.2.3 08:00:27:2e:d3:9f#MISSION ACOMPLISHEDNOW Improving the Program Using a List of Dictionaries#CODE:
- # !/usr/bin/evn python
- import scapy.all as scapy
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- arp_request_broadcast = broadcast/arp_request
- answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0]
- clients_list = []
- for element in answered_list:
- clients_dict = {"ip":element[1].psrc, "mac":element[1].hwsrc}
- clients_list.append(clients_dict)
- return clients_list
- def print_result(result_list):
- print("IP\t\t\tMAC Addres\n-------------------------------")
- for client in result_list:
- print(client["ip"] + "\t\t" + client["mac"])
- scan_result = scan("10.0.2.1/24")
- print_result(scan_result)
#ASSIGMENT!
- #!/usr/bin/env python
- # Network scanner
- import scapy.all as scapy
- import optparse
- def get_arguments():
- parser = optparse.OptionParser()
- parser.add_option("-t", "--target", dest="target", help="Target IP / IP range.")
- options, arguments = parser.parse_args()
- return options
- def scan(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- arp_request_broadcast = broadcast / arp_request
- answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0]
- clients_list = []
- for element in answered_list:
- client_dict = {"ip": element[1].psrc, "mac": element[1].hwsrc}
- clients_list.append(client_dict)
- return clients_list
- def print_result(results_list):
- print("IP\t\t\tMAC Address\n-------------------------------")
- for client in results_list:
- print(client["ip"] + "\t\t" + client["mac"])
- options = get_arguments()
- scan_result = scan(options.target)
- print_result(scan_result)